Cybersecurity in 2026 is no longer a background IT function. It has become a cornerstone of modern business strategy. With global operations running on interconnected digital ecosystems, one attack can cascade through entire industries. Organizations today are judged not only by their products and services but also by how well they protect customer data, ensure business continuity, and maintain digital trust. The stakes are higher than ever: a single breach can collapse investor confidence, trigger regulatory penalties, and erase years of brand-building in days.
CTOs and IT Managers tasked with protecting expanding digital infrastructures.
Compliance Officers ensuring organizations meet growing regulatory demands.
Executives and Business Owners who understand that security underpins brand value and customer trust.
- Ransomware remains the most damaging threat, now employing double and triple extortion.
- AI is powering both cyberattacks and defenses, fueling an escalating digital arms race.
- Supply chain attacks exploit weak vendor security, requiring transparency and monitoring.
Ransomware: The Evolving King of Threats
Ransomware has dominated the threat landscape for years, and in 2026 it remains the most profitable form of cybercrime. What has changed is the sophistication of these attacks. Criminal groups now run ransomware operations like businesses — with structured negotiation teams, 24/7 “customer service” for victims, and tiered ransom demands based on company size and data sensitivity.
The classic approach of encrypting data is no longer enough for attackers. Modern ransomware employs double and triple extortion tactics: first, data is encrypted; second, it is stolen and threatened to be leaked; third, attackers may launch a DDoS attack to amplify the damage and urgency.

Hospitals, banks, and manufacturers are prime targets because downtime in these industries is catastrophic both financially and socially.
What makes ransomware particularly devastating is its unpredictability. Even organizations with backups may find themselves compromised if attackers threaten to leak intellectual property or sensitive customer records. Defenses now revolve around segmented storage, zero-trust architectures, and automated anomaly detection to catch intrusions before encryption takes place.
AI-Powered Cyberattacks: The New Arms Race
Artificial intelligence is transforming the battlefield. Cybercriminals now use AI to scale and personalize attacks at speeds no human could match. Phishing emails generated by AI are nearly indistinguishable from genuine business correspondence. Voice deepfakes trick executives into authorizing fraudulent wire transfers. Video manipulations allow attackers to impersonate trusted figures in real time.
Worse still, AI-powered malware can continuously adapt its code, changing signatures to evade traditional detection systems. Attackers can deploy swarms of automated bots to probe vulnerabilities across thousands of systems simultaneously.
On the other side, defenders are also deploying AI — building predictive systems that analyze patterns of network activity and detect subtle anomalies. But this is an arms race: as defense systems get smarter, so too do the offensive algorithms. The key challenge for enterprises in 2026 is ensuring that their AI defense is proactive, not just reactive.
Supply Chain Attacks: Exploiting the Weakest Link
Modern businesses rarely operate in isolation. From cloud providers to software vendors and logistics partners, every organization is part of a vast and complex supply chain. Attackers have learned that breaching a single weak link can grant them access to dozens of larger targets.
Recent years have shown examples of compromised software updates, malicious code hidden in popular open-source libraries, and stolen credentials from third-party contractors. These attacks spread silently, often going undetected until significant damage has been done.
Defending against supply chain risks requires deep vendor vetting, constant monitoring of third-party integrations, and adoption of Software Bill of Materials (SBOM) standards to maintain transparency. Businesses must now treat supplier security as part of their own.
Cloud and API Exploits: Expanding the Attack Surface
As organizations migrate to multi-cloud infrastructures and API-first architectures, their digital ecosystems have expanded exponentially — along with the opportunities for attackers. Misconfigured cloud storage, over-permissive access controls, and insecure APIs are now leading causes of breaches.
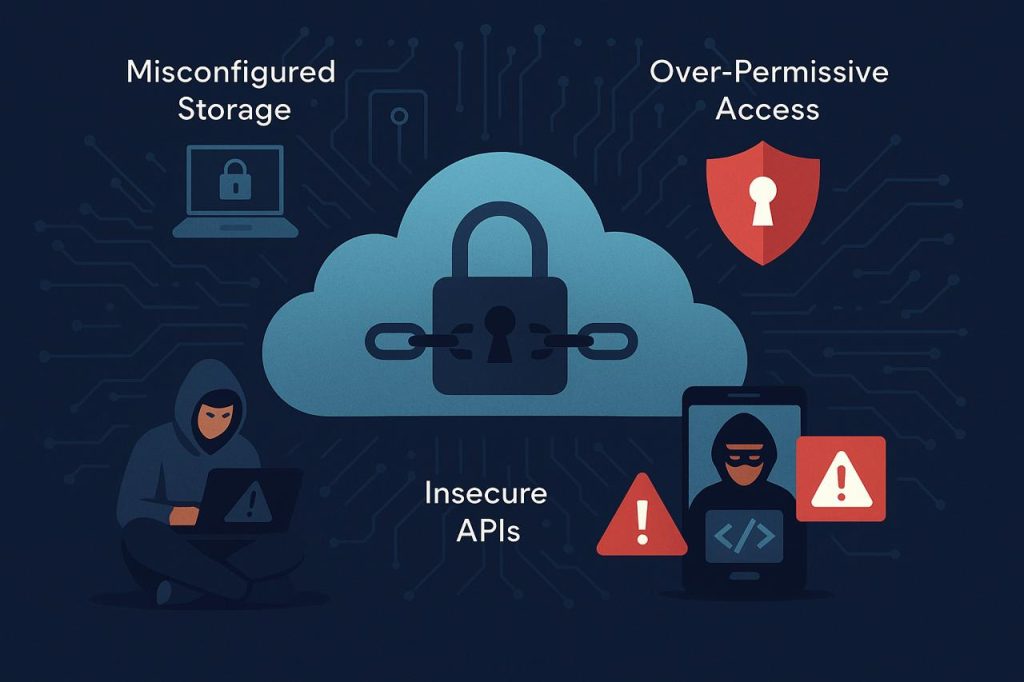
APIs are particularly dangerous because they form the backbone of mobile apps, financial platforms, and e-commerce systems. Attackers exploit weak authentication, missing rate limits, or poor input validation to gain entry. A single compromised API endpoint can expose entire databases of user information.
In response, forward-thinking companies are adopting continuous configuration scanning, strict authentication standards like OAuth 2.0 and JWT, and AI-based monitoring of traffic patterns to detect anomalies in real time. Cloud-native firewalls and API gateways provide another layer of defense, ensuring policies are consistent across distributed systems.
Insider Threats: The Human Factor
While external attackers dominate headlines, many of the most damaging breaches originate from within. Insider threats can be intentional — a disgruntled employee leaking sensitive data — or unintentional, such as careless workers clicking on malicious links. The rise of hybrid and remote work has made insider monitoring even more difficult, as employees access systems from varied devices and networks.
Enterprises are addressing insider risks with behavioral analytics, role-based access controls, and privileged access management. Training also plays a vital role: employees must understand how their actions can create vulnerabilities. Trusting staff remains essential, but that trust must now be reinforced with intelligent oversight.
The Future of Cybersecurity in 2026 and Beyond
Looking ahead, cybersecurity is moving from defense to prediction. Organizations are investing in AI-driven forecasting systems capable of identifying attack vectors before they are exploited. Regulatory frameworks such as the EU Cyber Resilience Act and U.S. federal mandates are raising global standards, pushing companies to embed compliance into every product from the start.
Cyber insurance providers are also reshaping the landscape, requiring stricter security protocols before issuing coverage. Meanwhile, international cooperation among governments is growing, as cybercrime increasingly transcends borders.
The future belongs to businesses that view cybersecurity not as a cost center but as a core value proposition. Strong security is now a driver of customer trust, investor confidence, and competitive advantage.
The biggest threat to cybersecurity is complacency — attackers innovate daily, so defenses must evolve faster.
Kevin Mitnick, Security Consultant
Conclusion
Cybersecurity in 2026 is defined by complexity and speed. Ransomware continues to evolve with double- and triple-extortion tactics, while AI-powered attacks are rewriting the rules of deception and speed. Supply chain vulnerabilities, cloud/API exploits, and insider threats further expand the attack surface, leaving no industry untouched.
For businesses, the path forward is not just stronger firewalls or bigger budgets — it is a mindset shift. Zero Trust architectures, predictive AI-driven defenses, and proactive governance must become standard practice. Companies that prioritize cybersecurity as a core business function, not just a technical layer, will be the ones that thrive in this environment.
Cybersecurity is no longer a “back-office” issue. It is now a boardroom topic, a customer expectation, and a defining factor of long-term competitiveness.
Why Ficus Technologies?
At Ficus Technologies, we help companies transform cybersecurity from a defensive necessity into a competitive edge.
Our expertise covers:
- Secure-by-design architectures for mobile, cloud, and enterprise systems.
- Advanced penetration testing and continuous threat monitoring.
- AI-driven defense strategies tailored to evolving risks.
- Full compliance support for global standards, including GDPR, HIPAA, and ISO.
We don’t just secure systems — we secure the future of your business.
Because attackers now use multi-layered tactics — encrypting data, threatening to leak it, and launching DDoS attacks simultaneously to maximize pressure on victims.
Yes. AI can generate hyper-realistic phishing, create deepfakes in real time, and adapt attack strategies instantly, making defenses far more difficult.
By auditing vendor security, enforcing contractual cybersecurity standards, and using monitoring tools that provide visibility into third-party risks.
APIs. Poorly secured APIs are now the main entry points for hackers into mobile, SaaS, and cloud platforms.
It’s massive. Insiders often have legitimate credentials, making their actions harder to flag. Both malicious actors and careless employees can trigger catastrophic breaches.