In 2026, mobile applications dominate nearly every aspect of digital life. From banking and healthcare to entertainment and logistics, users rely on apps for convenience, speed, and accessibility. But with this dependence comes a rising tide of cyber threats. Every mobile app becomes a potential entry point for attackers if not designed and maintained with strong security in mind. Businesses that fail to prioritize security don’t just risk data breaches — they risk customer trust, reputation, and regulatory penalties.
CTOs and product managers seeking to balance speed of delivery with enterprise-grade protection.
Cybersecurity professionals who need insights into the latest practices shaping mobile defense.
- Mobile app security is essential, not optional, in 2026.
- Core practices include secure coding, authentication, encryption, API protection, and monitoring.
- Trends like Zero Trust and AI-driven defense define the future of app protection.
Why Mobile App Security Matters
The scale of cyberattacks on mobile platforms has reached record levels. Studies show that more than 70% of mobile apps contain at least one critical vulnerability, and the global average cost of a breach has surged to $4.5 million. For industries such as finance and healthcare, a single security lapse can have catastrophic consequences.
When users install an app, they expect privacy, safety, and reliability. If their personal or financial data is compromised, they rarely give the brand a second chance. This makes security not just a technical requirement, but the cornerstone of long-term customer loyalty.
Secure Coding from the Start
Mobile security begins long before an app reaches the App Store or Google Play — it starts in the code editor. In 2026, the majority of mobile vulnerabilities still trace back to careless coding practices. A missing input validation rule, an exposed API key, or a failure to encrypt sensitive fields can give cybercriminals exactly the gap they need.
By treating security as part of the architecture rather than an afterthought, companies save themselves from both technical debt and reputational damage. Secure coding today means embedding validation logic in every form field, encrypting sensitive values even in memory, and using modern obfuscation techniques to make reverse engineering almost impossible. Forward-looking teams also rely on automated code review tools and static analysis scanners that continuously flag weak points before release. This shift-left mindset ensures that apps are designed with resilience at their core, turning security into a structural feature rather than a patch.
Authentication and Access Control
As digital identities grow more valuable, protecting them has become one of the highest priorities in mobile security. Passwords, once the main defense, are no longer enough. In 2026, users expect biometric authentication as a standard feature, whether through a fingerprint scan, facial recognition, or voice ID. Beyond that, secure apps employ adaptive authentication that evaluates user behavior in real time.
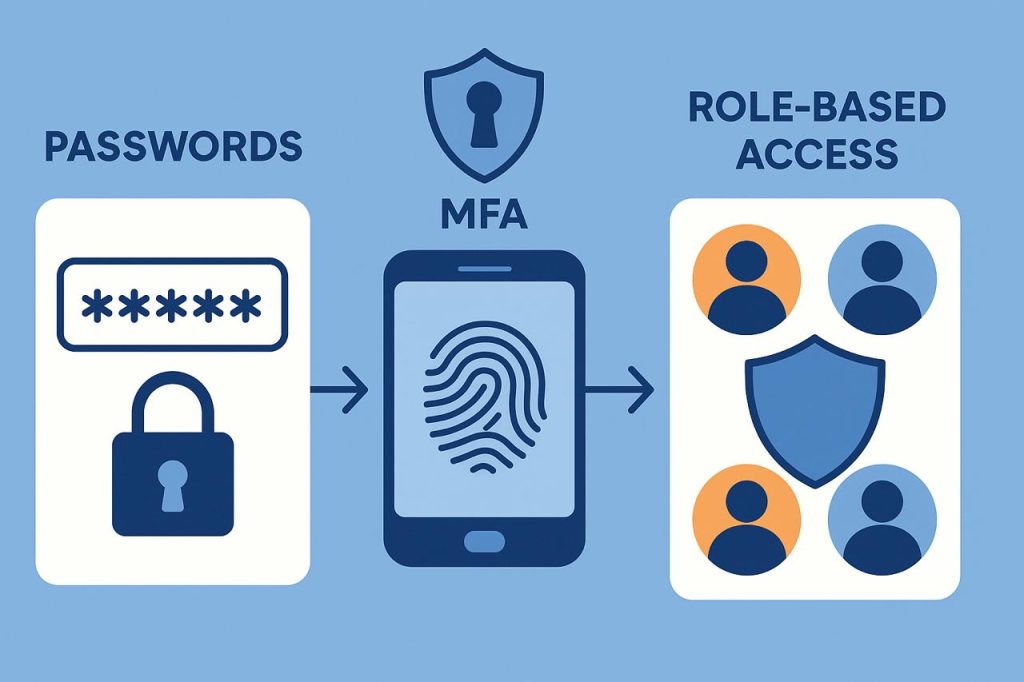
Session management has also matured: apps automatically log users out after periods of inactivity and detect suspicious behavior, such as logins from unusual geographies. Role-based access systems ensure that employees, customers, and partners only see what they are entitled to — nothing more. Together, these measures create a layered security model that frustrates attackers while reassuring users that their identities are safeguarded at every step.
Data Encryption Everywhere
The value of mobile apps lies in the sensitive data they process — financial records, health details, personal conversations. But without encryption, this data is essentially an open book. In 2026, encryption has become not just a best practice but an industry baseline. Data in motion is protected with advanced transport protocols like TLS 1.3 and beyond, ensuring that no one can intercept communication between app and server. Data at rest, whether on devices or cloud servers, is safeguarded with AES-256 encryption or stronger methods.
What’s equally important is a minimalist storage philosophy: responsible apps avoid storing sensitive data locally unless absolutely necessary. This reduces the attack surface significantly. End-to-end encryption for communications has also become standard, giving users confidence that their messages and transactions remain unreadable to outsiders — even to the service provider itself.
API Security as a Priority
Every modern mobile app is powered by APIs. They connect payments, analytics, cloud storage, third-party integrations, and more. But the same APIs that make apps dynamic also make them vulnerable. In fact, API endpoints are now the number one entry point for attackers.

In 2026, responsible development teams treat API defense as mission-critical. They implement strict authentication for every request, deploy rate limiting to resist brute-force and denial-of-service attempts, and rely on intelligent monitoring systems that flag anomalies in real time. Many companies also use API gateways to enforce consistent policies across the ecosystem, centralizing defense rather than leaving individual developers to patch vulnerabilities on their own. Without robust API protection, even the most polished apps risk being dismantled from the inside.
Continuous Testing and Monitoring
Cybersecurity does not end with launch day. Once an app is in the hands of users, it enters a hostile environment where attackers constantly look for new ways to exploit it. The only way to stay ahead is through continuous testing and monitoring.
Modern enterprises now build penetration testing into every development cycle, simulating real-world attack scenarios to identify weak spots. Security is integrated into CI/CD pipelines so that vulnerabilities are patched within hours, not months. Automated dependency checks scan third-party libraries for outdated or malicious components, while monitoring dashboards track anomalies in real time. This proactive posture ensures that threats are addressed before they escalate into breaches, protecting both users and the business from costly incidents.
Trends in Mobile App Security 2026
By 2026, security has shifted from being reactive to predictive. Zero Trust frameworks — where no device, user, or request is assumed safe — are becoming the standard for enterprise apps. Artificial intelligence plays a central role, detecting anomalies across millions of interactions and stopping threats before they succeed.
The rise of DevSecOps ensures that security checks are baked into every sprint, rather than squeezed in at the end of development. At the same time, industries like finance and healthcare are adopting a regulation-first mindset: apps are now built with compliance requirements in mind from day one, reducing the risk of penalties and making audits smoother. The trend is clear: security is no longer a gate at the end of the pipeline — it is the bloodstream of digital product development.
Secure your app with Ficus Technologies!
Contact UsReal-World Impact
Strong security is not just about protecting data — it is about enabling business growth. Companies with secure apps face fewer breaches, saving millions in potential fines and losses. More importantly, they build trust, which translates into higher customer retention and stronger brand reputation. A bank with robust mobile security attracts more users. A healthcare app that proves compliance with regulations gains quicker adoption in hospitals. An e-commerce platform that ensures safe transactions becomes the preferred choice for global buyers.
In a market where users can delete one app and download a competitor in seconds, security is a differentiator. Businesses that treat it as an integral part of user experience stand out, while those that neglect it quickly fall behind. In 2026, mobile app security is not just a defensive measure — it is a competitive weapon.
Conclusion
By 2026, mobile app security has evolved into a defining factor of digital success. It is no longer an isolated technical concern managed by IT teams at the end of development — it is a continuous, integrated discipline that touches every stage of the product lifecycle. From secure coding practices and advanced authentication to API hardening and predictive anomaly detection, the measures outlined in this article reflect how modern security has become both proactive and intelligent.
The real impact, however, lies beyond technology. Businesses that prioritize mobile app security gain more than protection from breaches — they win customer trust, regulatory confidence, and long-term market resilience. In an era where one vulnerability can erase years of brand equity, investing in security is the smartest business decision companies can make.
Why Ficus Technologies?
At Ficus Technologies, we know that security is not an afterthought — it is built into every solution we deliver.
Our teams design secure-by-default architectures:
- Run penetration tests and continuous monitoring.
- Deliver compliance-ready apps for industries like healthcare and fintech.
- Integrate AI-powered security tools for future-proof defense.
With us, mobile apps are not only innovative but also unshakably secure.
Unsecured APIs and weak authentication are the top risks.
At least twice a year and after every major update.
Yes. Scalable, cloud-native tools make enterprise-grade protection affordable.
Penalties include fines, app removal from stores, and permanent loss of customer trust.